How does Jigit ensure proper performance?
Here you can find performance considering for Jigit. Includes information about frequency of indexing and requests to the 3rd party system.
Jigit respects the API rate limits. When it gets throttled, it delayed the new requests.
Jigit App uses GitLab/GitHub REST APIs to index commit messages against Jira issues. Those APIs can be throttled. As a result, the indexing should be spread over time to smooth the load. Otherwise, Git systems will reject requests of Jigit.
It is done in the following way:
There is a scheduled task that runs every 2 minutes (can be changed with
moveworkforward.jigit.index.interval)It checks the head commit and indexes it. Indexing works the following way:
extracts Jira issue keys;
stores those in the database together with the commit information;
adds to the internal queue the next commit (if it was not indexed before);
sleeps every X requests to the GitLab (configurable).
If a commit had been indexed, the whole index process for that branch/repo combination stops
The scheduled task is run from 1 Data Center node (in the case of Jira Data Center multi-node deployment).
Throttling related parameters
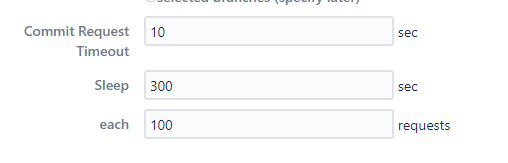
Commit Request Timeout- tells for how long the connection should be open to calling the GitHub/GitLab API before it times out. Default and recommended - 10 seconds.Sleep- the time Jigit will sleep between request batches (controlled by parameter each X request). The default and recommended value is 10.Each X requests- is the number of requests in each request branch before the sleep. The default and recommended value is 10.
The logic behind those values is:
GitHub has a limit of 5000 requests per hour per agent (Jigit is an Agent in this case), which is around 83 per minute. With the default settings, Jigit may execute 60 requests per minute, which is close, but still below 83.
Other performance considerations:
when the App runs the first time, it may take a while to index an old repository with multiple commits;
there is a scheduled task per each configuration rule.
Official Rate limits by systems
GitHub - https://docs.github.com/en/rest/rate-limit?apiVersion=2022-11-28
GitLab - https://docs.gitlab.com/ee/security/rate_limits.html
On-Premise instances could have those settings tweaked.
Updated:
