Bitbucket Post Webhook - Mutual TLS
Bitbucket Post Webhooks supports mutual TLS and in this article you can find more details on how to set it up.
Below you can find how to setup mutual TLS between Jenkins and Bitbucket Post Webhook plugin.
Server key store and trust store
Create directory “server/cert”, then run next commands
keytool -genkeypair -keyalg RSA -keysize 2048 -alias server -dname "CN=Hakan,OU=Amsterdam,O=Luminis,C=NL" -ext "SAN:c=DNS:localhost,IP:127.0.0.1" -validity 3650 -keystore server/cert/identity.jks -storepass secret -keypass secret -deststoretype pkcs12
keytool -exportcert -keystore server/cert/identity.jks -storepass secret -alias server -rfc -file server/cert/server.cer
keytool -keystore client/cert/truststore.jks -importcert -file server/cert/server.cer -alias server -storepass secretClient key store and trust store
Create directory “client/cert”
keytool -genkeypair -keyalg RSA -keysize 2048 -alias client -dname "CN=Suleyman,OU=Altindag,O=Altindag,C=NL" -validity 3650 -keystore client/cert/identity.jks -storepass secret -keypass secret -deststoretype pkcs12
keytool -exportcert -keystore client/cert/identity.jks -storepass secret -alias client -rfc -file client/cert/client.cer
keytool -keystore server/cert/truststore.jks -importcert -file client/cert/client.cer -alias client -storepass secretStart Jenkins with certificates
To start Jenkins we use docker image with required parameters.
docker run -it \
-p 8083:8083 \
-p 8080:8080 \
--name jenkins \
-v server/cert:/cert \
--env JAVA_OPTS="-Djavax.net.ssl.trustStore=/cert/truststore.jks -Djavax.net.ssl.trustStorePassword=secret" \
--env JENKINS_OPTS="--httpPort=8080 --httpsPort=8083 --httpsKeyStore=/cert/identity.jks --httpsKeyStorePassword=secret" jenkins:2.60.3Jenkins accepts connection on http and https ports.
-Djavax.net.ssl.trustStore=/cert/truststore.jks -Djavax.net.ssl.trustStorePassword=secret - replaces default Java trust store
--httpsKeyStore=/cert/identity.jks --httpsKeyStorePassword=secret - specifies key store for Jenkins
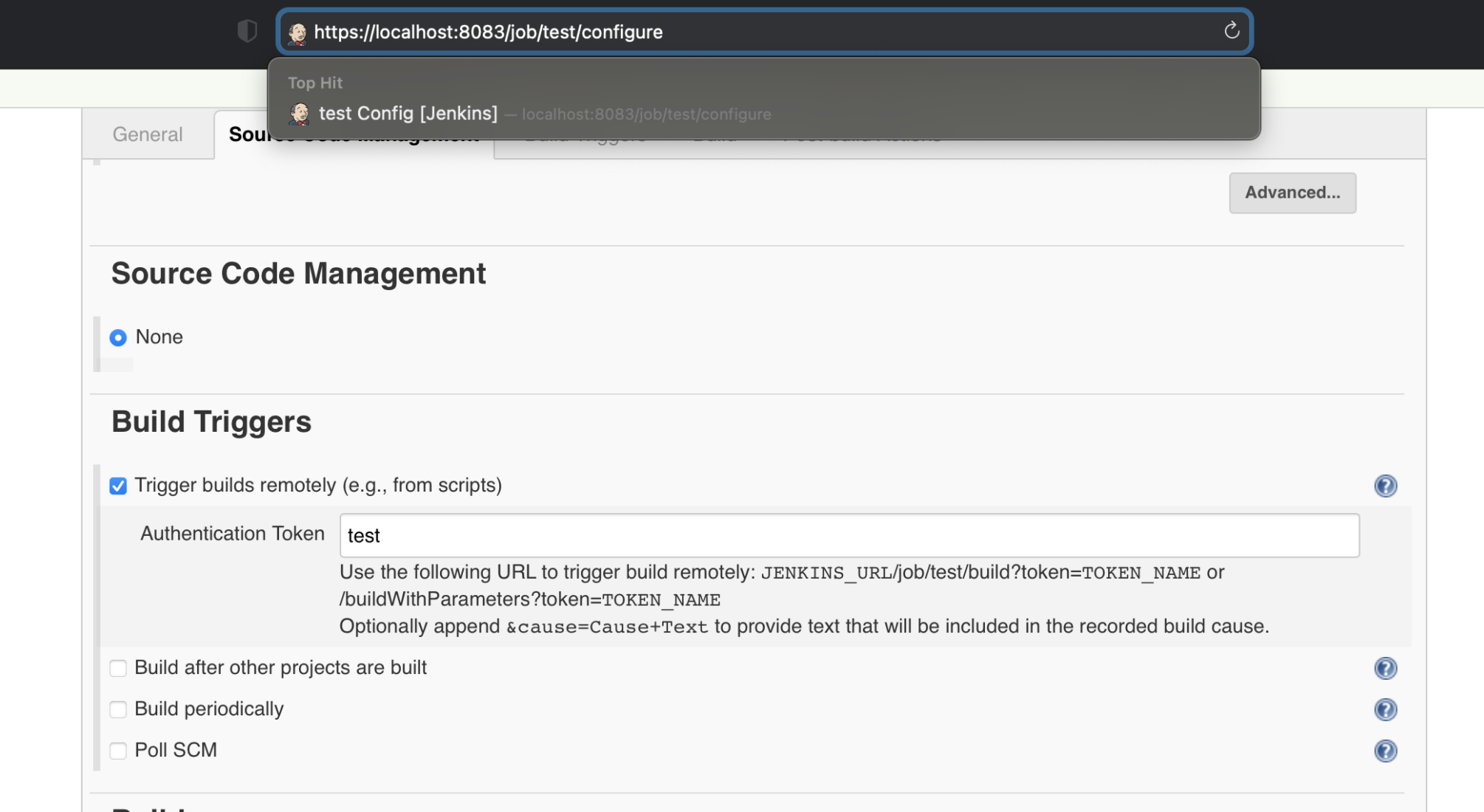
After setup the project is complete, build can be triggered by REST: JENKINS_URL/job/test/build?token=TOKEN_NAME or /buildWithParameters?token=TOKEN_NAME
Bitbucket Post Webhook plugin
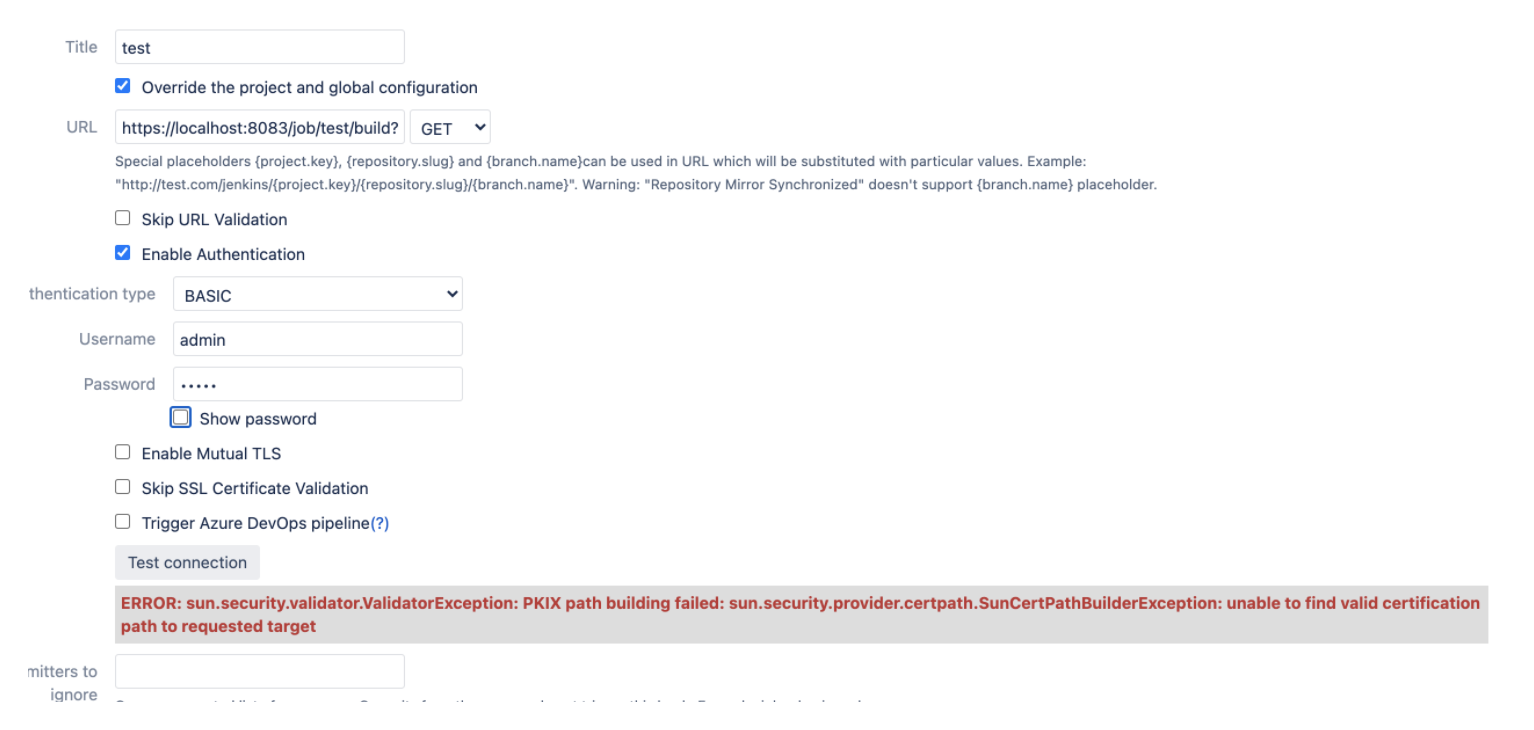
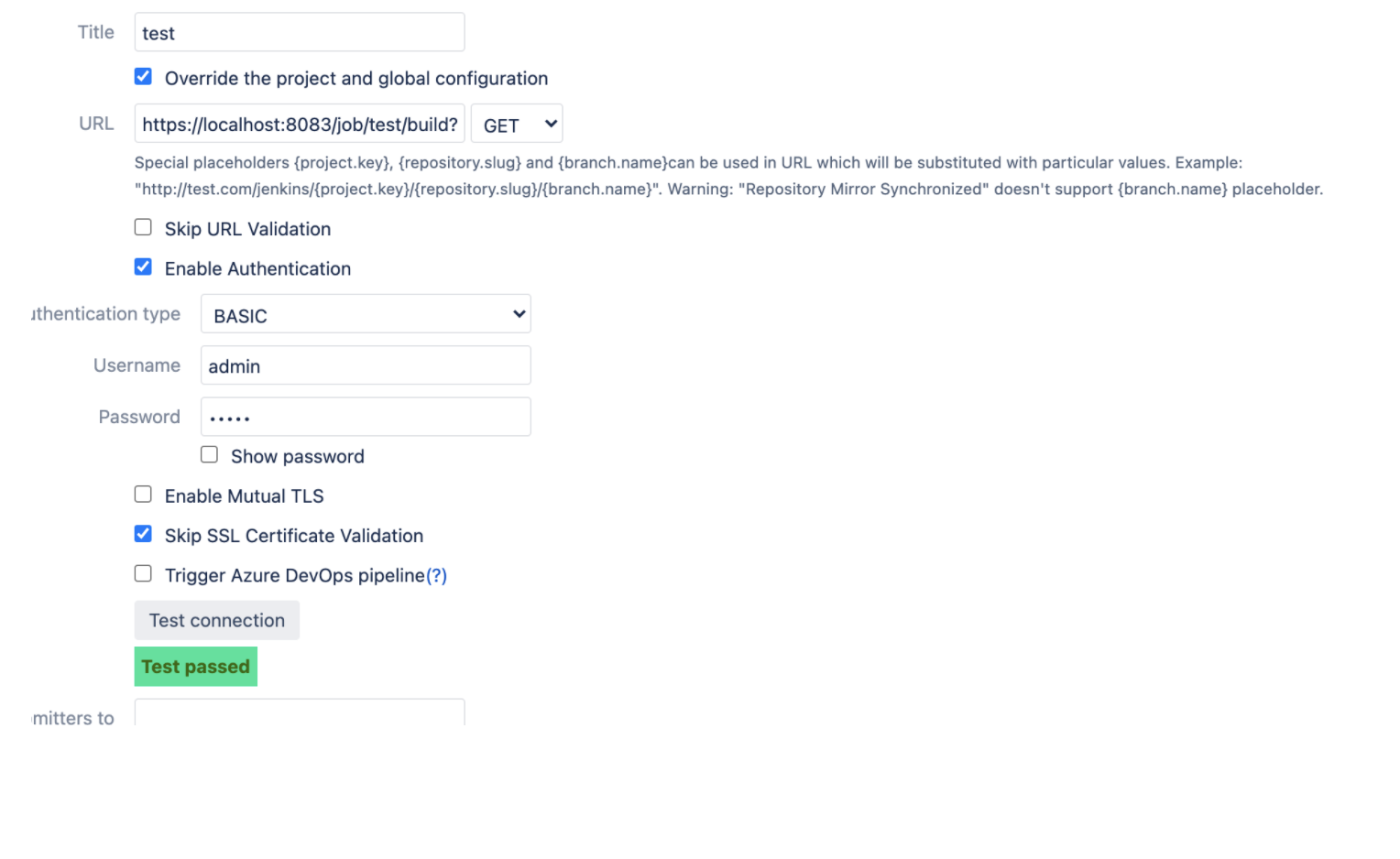
To check if URL can be handled “Test connection“ button can be used.
In all cases authentication is required.
HTTPS URL without additional parameters:
HTTPS URL with “Skip SSL Certificate Validation“:
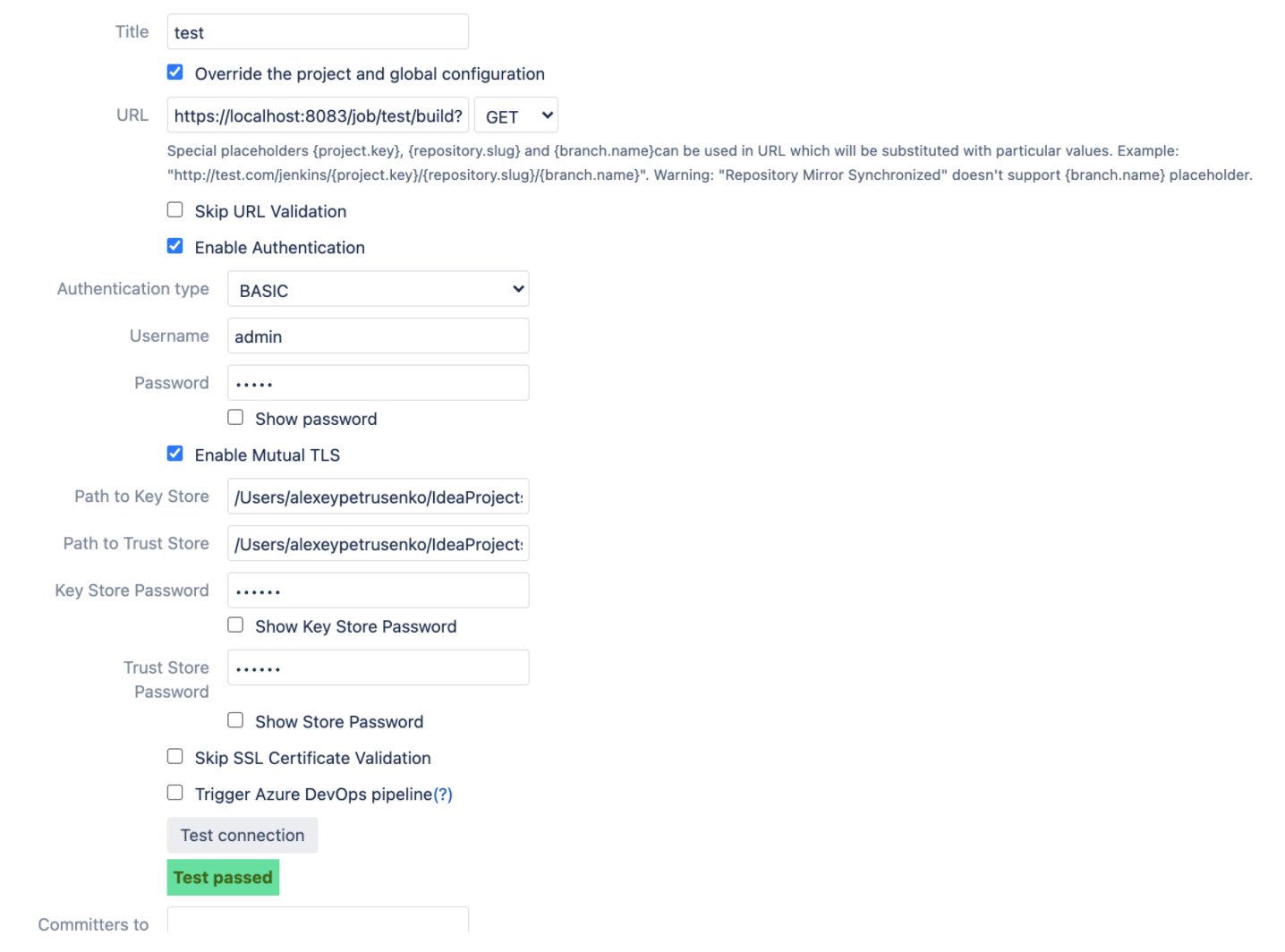
HTTPS URL with “Enable Mutual TLS“:
Key Store and Trust Store files should be on the same box where Bitbucket is running.
Path to Key Store - client/cert/identity.jks
Path to Trust Store - client/cert/truststore.jks
Key Store and Trust Store Passwords - secret
Results can be checked at Jenkins:
References:
https://hub.docker.com/_/jenkins/
https://support.cloudbees.com/hc/en-us/articles/203821254-How-to-install-a-new-SSL-certificate
https://stackoverflow.com/questions/40126736/enable-https-in-jenkins
