Microsoft Teams Jira Atlassian 2-way Connection Architecture
Microsoft Teams 2-way integration with Atlassian Server and Data Center products
If you have any questions or comments please do not hesitate to contact us.
Objective
This light document provides high-level architecture and security consideration of implementing 2-way/bi-directional integration between Microsoft Teams (cloud chat system) and an Atlassian product like Jira, Confluence, Bitbucket or Bamboo.
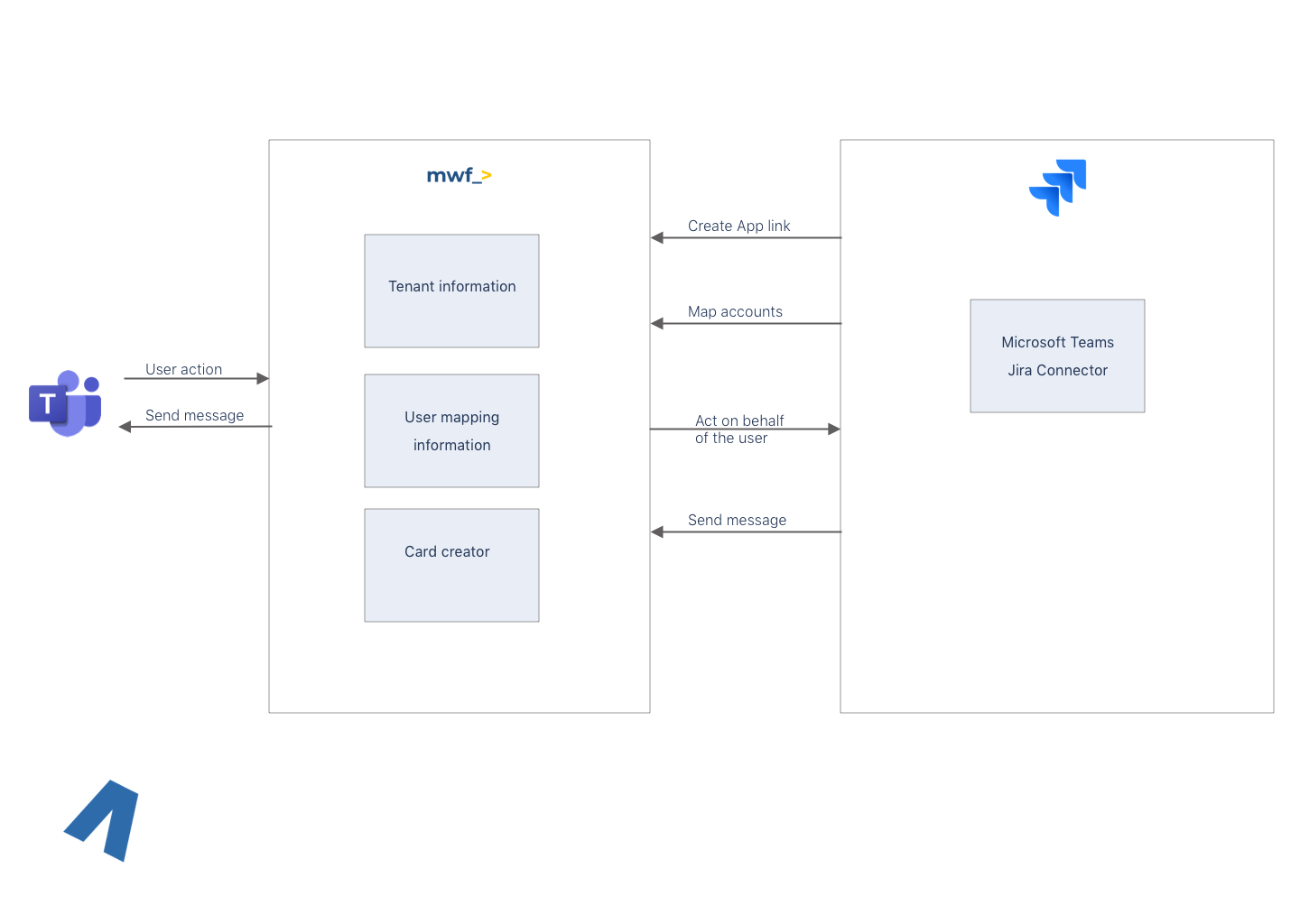
Architecture
Below you can see a very high-level architecture of a bi-directional integration between Jira and Microsoft Teams.
There are following known limitations:
An external system cannot call Jira’s REST APIs without being authenticated.
There are two ways to authenticate:
an API token to act on behalf of a user
OAuth2.0 handshake with a token exchange. This way is the only way for a 3rd party App to call Jira on behalf of an App and not a concrete user.
When a user in Microsoft Teams acts, for instance, comments a ticket, we must make a comment in Jira on behalf of the Jira’s user. As a result, mapping of Microsoft Teams and Atlassian user required and stored to act on behalf of a user. The mapping will be stored encrypted in the MWF system.
Jira has to have 443 port exposed to MWF list of IPs and have a valid SSL certificate for HTTPS communication.
MWF system needs to know the list of IPs of customer’s Jira to permit the communication and have a valid SSL certificate for secure communication
We are in contact with Atlassian to find out if there is a way to build a 2-way integration without an intermediary system.
Security considerations
To warranty the highest security Move Work Forward provides the following:
Customers/tenants can choose whether they want to be in a multi-tenant system or a single-tenant system. The preferable way is to use a single-tenant system, but it will require additional provisioning (it may require an additional charge).
The Customer in Jira must create an Application link for Move Work Forward system to communicate with Jira.
IP-address whitelisting used in Move Work Forward system and Jira servers network to decrease the security surface.
TSL communication used to protect data in transfer.
All tenant data is encrypted at rest with tenant/customer-specific AWS KMS key.
There is no sensitive data stored in MWF system, except the token to access Jira.
Updated:
