Frequently asked security questions
This is the guide for Azure DevOps for Jira application that bring development information from Microsoft Azure DevOps to Atlassian Jira Cloud.
If you are looking for Jira Data Center and Azure DevOps integration, check out Jigit.
Video guide
https://www.youtube.com/watch?v=YmmsldnEobYAzure DevOps for Jira by Move Work Forward
e-Cyber Security Questions
Q: Is data stored outside of Atlassian products?
A: We store the Personal Access Token and some metadata in our encrypted storage.
Q: Which data can this app read/write?
A: Currently, Azure DevOps for Jira needs the following read-only scopes for the Personal Access Token - Code, Build, Release. The global configuration permissions does not write anything. The only write option available is for the end user from the Jira issue view when a feature branch is created. For this operation, the end-user needs to login with his/her Azure DevOps credentials.
Q: Are there additional compliance certifications?
A: Move Work Forward is SOC 2 Type II Compliance. You can learn more in our Trust Center provided by Vanta - https://trust.moveworkforward.com/
Additionally, we participate in Cloud Fortified and Bug Bounty programs.
Q: Is DPA available?
A: Yes, https://www.moveworkforward.com/license-agreement/data-protection-agreement is the draft and we need to sign it with each company separately. You can find the link in the footer of our website.
Q: What is the classification of data involved?
A: We query or receive via subscriptions/webhooks payloads from Microsoft that pay contain user data. It is the data about pushes, pull requests, branches and pipeline runs. It passes our system, so it can be logged in AWS Cloud Watch (we have 7 days retention).
Q: Who is data owner / data controller / data processor?
A: We are the data processor.
Q: Accesses via which devices: mobile devices, private devices, company devices?
A: As of , only 3 people have production access from company laptops. We adhere to all SOC 2 Type II compliance requirements.
Q: Operational concept regarding IT security check. Where are the servers located, subject of firewalls, virus scanners, patch process. What security certifications or security whitepapers can be provided by the vendor (ISO, ..)?
A: Our backend system is in AWS us-east-1 region. It is fully Serverless (AWS Lambda, API Gateway, SQS, DynamoDB). Every employee or contractor uses Vanta to monitor his/her laptop, we execute reference checks and constant security trainings.
Q: Are there Penetration test results provided by the vendor?
A: We use Bug Crowd Bug Bounty program that employs white-hat hackers to penetrate our apps. We don’t have a public report.
Q: Other service providers / data center operators involved ? If yes: description of processes and their IT security measures.
A: AWS, us-east-1 region.
Q: Could you please explain the setup architecture?
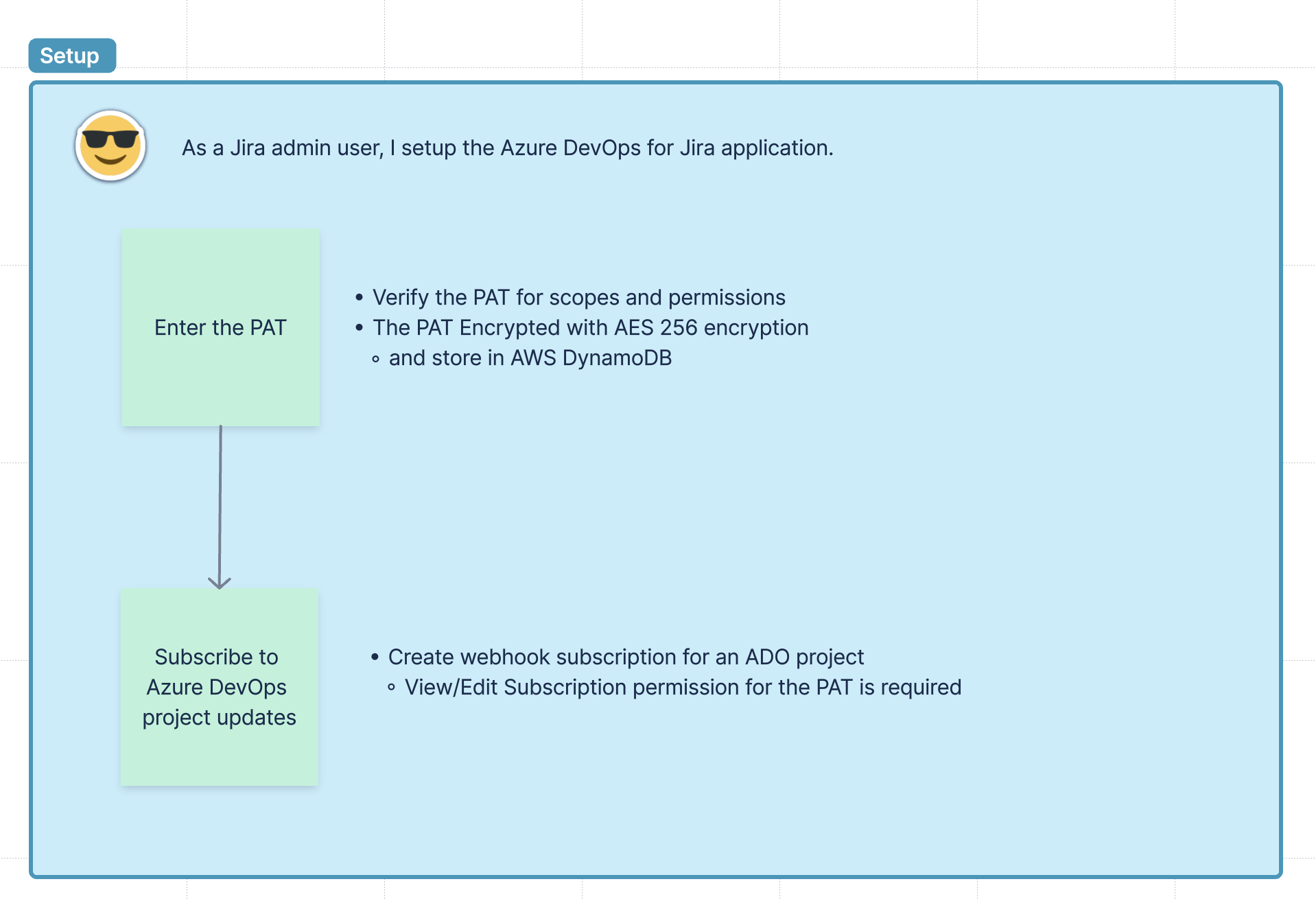
Q: What data is transferred and stored?
A: Move Work Forward stores only configuration related data and does not stores the processed data at all. It is either passed to Atlassian or ignored (if no matching issue key was found).
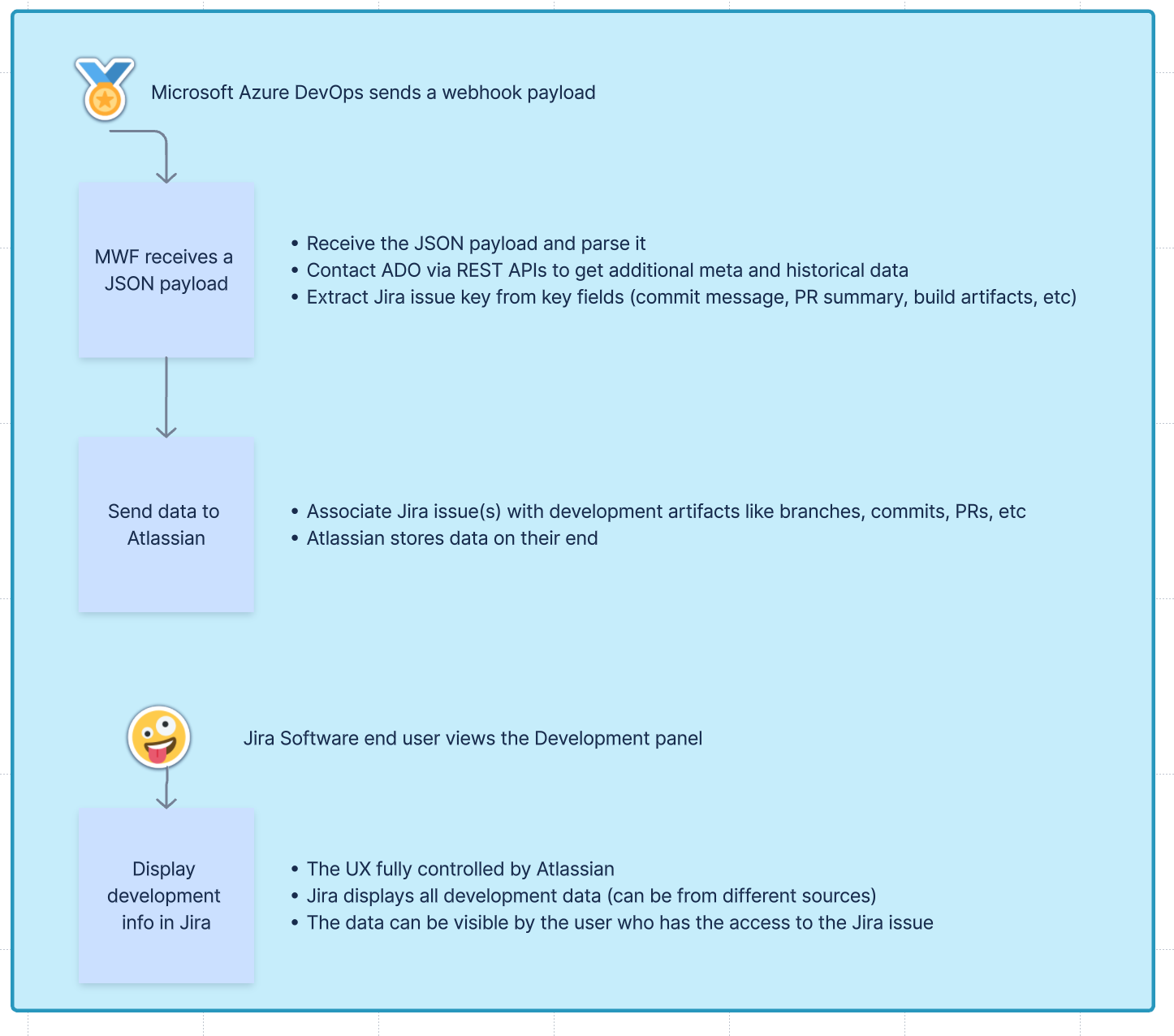
Q: What Encryption is used?
A: AES-256 encryption is used for the storage. SSL traffic is used for the communications.
Q: What is the location of the backend?
A: AWS us-east-1
Updated:
